地址
請求頭的X-sign需要逆向,斷點后找到 r["x-sign"] = s(e, t)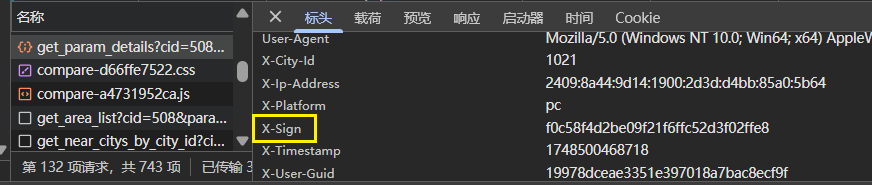
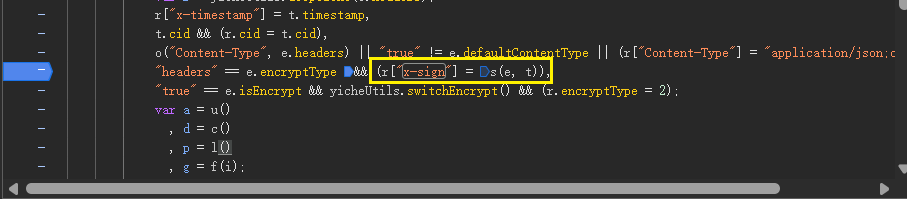
e和t參數直接從瀏覽器複製,進入s函數發現返回md5加密值,分析是否為標準md5,上面的if條件為true,所以else語句不用複製到本地。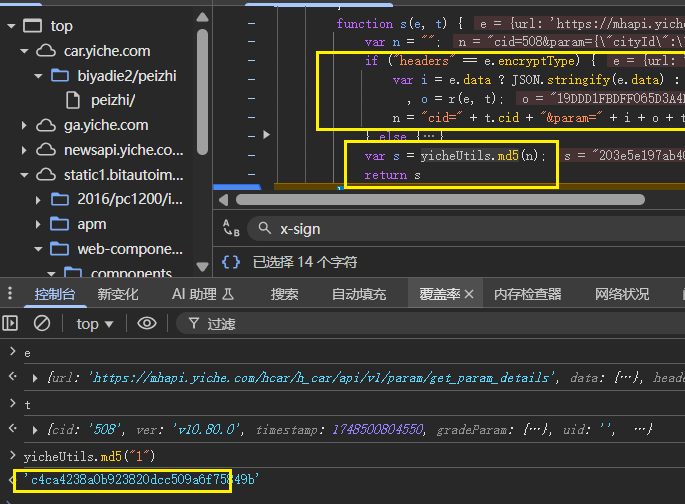
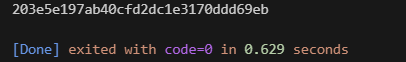
最終測試結果: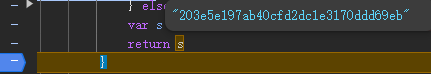
var crypto = require('crypto');
function md5(password) {
var md5 = crypto.createHash('md5');
return md5.update(password).digest('hex');
}
function r(e, t) {
if (!e.headers || !e.headers["x-platform"])
return t.cid;
var n = t.headerEncryptKeys.find(function (t) {
return t.name == e.headers["x-platform"]
});
return n ? n.value : "DB2560A6EBC65F37A0484295CD4EDD25"
}
function s(e, t) {
var n = "";
if (true) {
var i = e.data ? JSON.stringify(e.data) : "{}"
, o = r(e, t);
n = "cid=" + t.cid + "¶m=" + i + o + t.timestamp
} else {
var a = [];
a.push("cid=" + t.cid),
a.push("uid=" + t.uid),
a.push("ver=" + t.ver),
a.push("devid=" + (e.deviceId || "")),
a.push("t=" + t.timestamp),
a.push("key=" + t.paramsKey),
n = a.join(";")
}
var s = md5(n);
return s
}
function getSign(cityId, serialId, timestamp) {
e = {
"url": "https://mhapi.yiche.com/hcar/h_car/api/v1/param/get_param_details",
"data": {
"cityId": String(cityId),
"serialId": String(serialId)
},
"headers": {
"x-platform": "pc"
},
"method": "GET",
"withCredentials": "true",
"async": "true",
"isParam": "true",
"dataType": "json",
"defaultContentType": "true",
"encryptType": "headers",
"isEncrypt": "false",
"isBrush": "false",
"proxy": "false",
"timeout": 5000
}
t = {
"cid": "508",
"ver": "v10.80.0",
"timestamp": Number(timestamp),
"gradeParam": {},
"uid": "",
"headerEncryptKeys": [
{
"name": "pc",
"value": "19DDD1FBDFF065D3A4DA777D2D7A81EC",
"cid": "508"
},
{
"name": "phone",
"value": "DB2560A6EBC65F37A0484295CD4EDD25",
"cid": "601"
},
{
"name": "h5",
"value": "745DFB2027E8418384A1F2EF1B54C9F5",
"cid": "601"
},
{
"name": "business_applet",
"value": "64A1071F6C3C3CC68DABBF5A90669C0A",
"cid": "601"
},
{
"name": "wechat",
"value": "AF23B0A6EBC65F37A0484395CE4EDD2K",
"cid": "601"
},
{
"name": "tencent",
"value": "1615A9BDB0374D16AE9EBB3BBEE5353C",
"cid": "750"
}
],
"paramsKey": "f48aa2d0-31e0-42a6-a7a0-64ba148262f0"
}
x_sign = s(e, t)
return x_sign
}
console.log(getSign('99', '98', 1748501847773))