找到登陸包,看到需要兩個參數,comp_d 和 uLogin(下面password的加密算法相同。)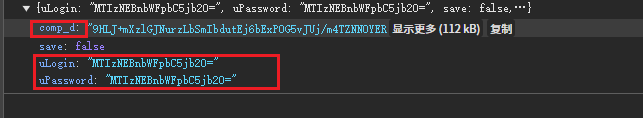
我先找的 uLogin,抓包定位,然後找到 crypt.encode 方法,跟進去,這個方法只會執行後面那個,所以從後面開始扒下。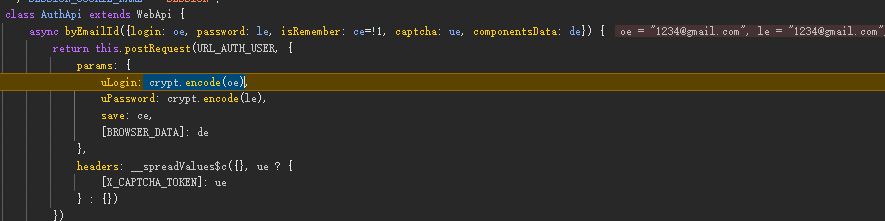
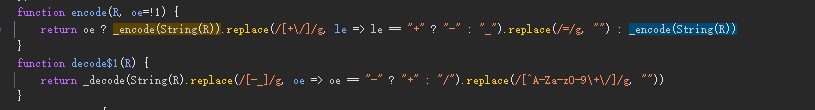
直接給出算法
cb_utob = function(R) {
let oe = null;
return R.length < 2 ? (oe = R.charCodeAt(0),
oe < 128 ? R : oe < 2048 ? fromCharCode(192 | oe >>> 6) + fromCharCode(128 | oe & 63) : fromCharCode(224 | oe >>> 12 & 15) + fromCharCode(128 | oe >>> 6 & 63) + fromCharCode(128 | oe & 63)) : (oe = 65536 + (R.charCodeAt(0) - 55296) * 1024 + (R.charCodeAt(1) - 56320),
fromCharCode(240 | oe >>> 18 & 7) + fromCharCode(128 | oe >>> 12 & 63) + fromCharCode(128 | oe >>> 6 & 63) + fromCharCode(128 | oe & 63))
}
re_utob = /[\uD800-\uDBFF][\uDC00-\uDFFFF]|[^\x00-\x7F]/g
utob = function(R) {
return R.replace(re_utob, cb_utob)
}
b64chars = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"
cb_encode = function(R) {
const oe = [0, 2, 1][R.length % 3]
, le = R.charCodeAt(0) << 16 | (R.length > 1 ? R.charCodeAt(1) : 0) << 8 | (R.length > 2 ? R.charCodeAt(2) : 0);
return [b64chars.charAt(le >>> 18), b64chars.charAt(le >>> 12 & 63), oe >= 2 ? "=" : b64chars.charAt(le >>> 6 & 63), oe >= 1 ? "=" : b64chars.charAt(le & 63)].join("")
}
btoa$1 = function(R) {
return R.replace(/[\s\S]{1,3}/g, cb_encode)
}
_encode = function(R) {
return btoa$1(utob(R))
}
console.log(_encode("1234@gmail.com"))JavaScript
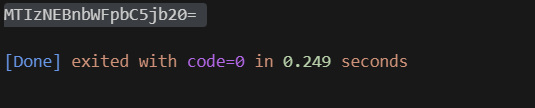
comp_d參數好像很麻煩,找了蠻久,文章就到這裏,待更新吧

